We are living at a time unprecedented on Earth.
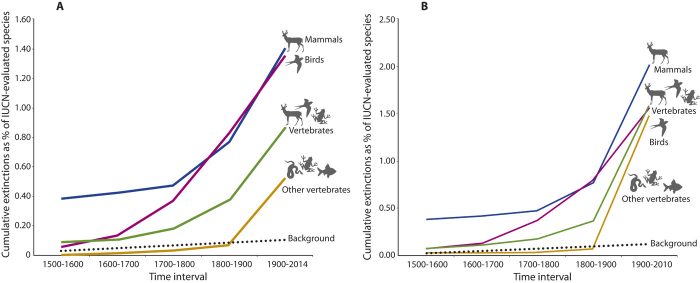
The year 2019 has confirmed that humanity’s collective activities have pushed Earth’s ecosystems towards the boundaries of what they can sustain.
In fact, for many ecosystems and species the boundary has already been crossed, and species are now vanishing at a rate higher than ever before in recorded history.
The realized threat of global warming
In addition to more obvious drivers of species extinction such as over-exploitation of natural resources and habitat loss caused by agriculture and other land development, the greatest immediate threat to the existing biosphere is global warming.
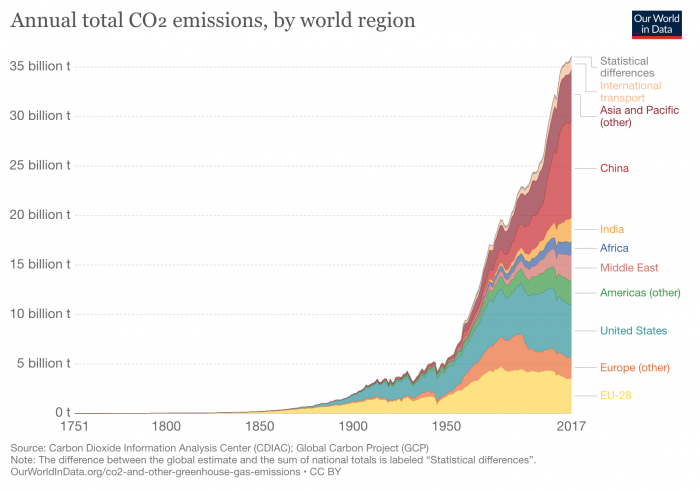
However, in spite of repeated and increasingly dire warnings from the scientific community for more than a century, greenhouse gas emissions from human activities have increased dramatically and continue to do so.
Already in 1896, Swedish scientist Svante Arrhenius (1859-1927) stated that a doubling of CO2 in the atmosphere would result in a global temperature increase of 5–6°C. Arrhenius’ results are in fact very close to our current climate models.
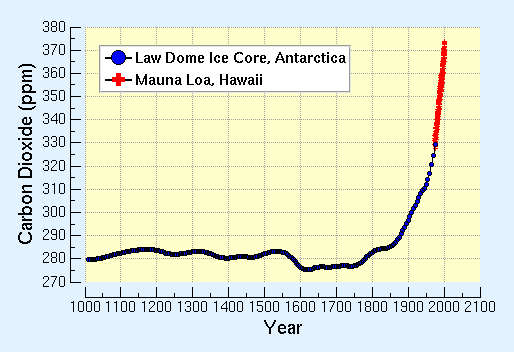
The benchmark for CO2 content in the atmosphere is the pre-industrial time, that is before about 1750, when the CO2 content is estimated to have been about 280 ppm (parts per million).
By 2017, the annual global average CO2 levels exceeded 400 ppm, which corresponds to the limit of 1.5°C set by the IPCC for keeping the climate changes under safe control. As of November 2019, this number has passed 410 ppm.
Last time the CO2 concentration was that high, horses and camels roamed the high Arctic and sea levels were at least 30 feet higher than today.
The fact that these changes are now happening more rapidly than in recorded history thus far means that many species and ecosystems that make up the biosphere are unable to adapt quickly enough.
A climate spinning out of control
The chemical composition of the atmosphere and the oceans are undergoing dramatic changes with accelerating positive feedback loops involving not only CO2 but methane, nitrogen, and sulfur as well as several other essential components.
These changes are causing the Earth’s biogeochemical cycles, and therefore the climate, to spin out of control.
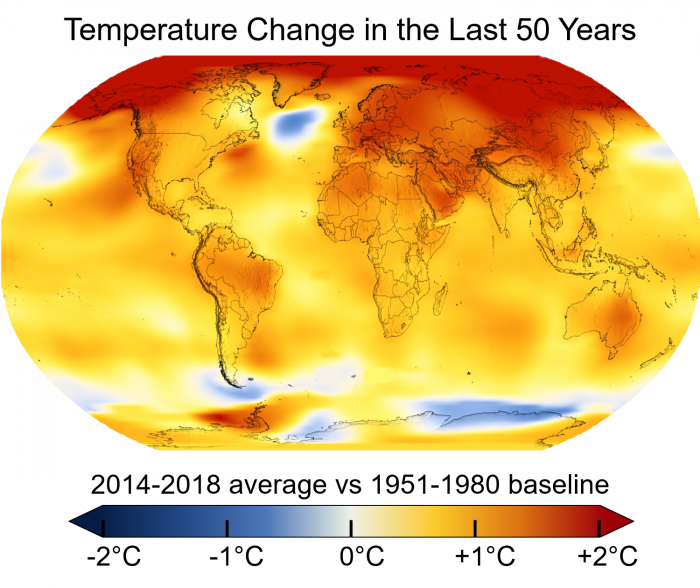
When the Earth’s temperature increases and its distribution is altered, it affects geophysical systems such as prevailing wind patterns and ocean currents — the global conveyor belt responsible for carrying salt, nutrients, and other essential chemical components upon which marine life depends.
The warmer climate not only melts sea ice and increases sea levels, but heats up wetland peat and thaws tundra in arctic regions which releases additional methane into the atmosphere.
Warmer oceans also absorb less oxygen, which leads to more anaerobic bacteria that produce toxic hydrogen sulfide gases that could have disastrous effects on existing organic life.
These global feedback systems and cycles are so large and complex that it can take decades or centuries for the consequences of our current emissions to take full effect.
This means that we are tipping the balance of the natural systems we depend on for survival and are pushing them to dangerous and unpredictable levels with possibly irreversible effects.
As a result the living Earth itself is turning into an unfamiliar environment that will be detrimental to life as we have known it.
The human race is heading for a disaster — a warned catastrophe, that is — and the entire remaining biosphere is at stake.
The consequences are already upon us
We are ending a year that has seen the most dramatic effects of climate change thus far, closing a decade with increasingly noticeable consequences of continually growing greenhouse gas emissions.
The direct effects are well-known by now and include physical impacts like the melting of ice sheets and subsequent sea level rise, as well as changes in ocean currents and weather patterns.
These impacts in turn lead to increased droughts, heat waves, and uncontrollable wildfires, as well as extreme flooding, cyclones, blizzards, and rainstorms with inevitable crop failures and global fish stock depletion as a result.

In addition to the catastrophic loss of biodiversity, the accelerating changes in our natural environment lead to regional famine, mass migrations, conflicts, and war between peoples fighting for dwindling resources.
Current mitigation plans are inadequate
According to the UN’s Climate Action Summit report we have until 2030 to cut CO2 emissions by 45% in order to limit global warming to 1.5°C . This entails a global average reduction of 4.5% per year over the next 10 years, while emissions on average have increased 1.5% annually in recent years.
This may not sound like much, but in reality it constitutes an enormous challenge on a scale unlike any we have successfully undertaken in the past.
The bottom line is that every person, every organization, every business, and every government have to do their uttermost to reduce their ecological footprint.
Although governments, large industrial companies, and international institutions can do the most to reduce hydrocarbon dependency and restore the depletion of natural resources that is taking place, even small contributions will have an effect — but we are short on time.
Our commitment
At Runbox we have decided to have a positive impact on the planet and our environment, and we want to achieve this with a net negative ecological footprint.
We will take responsibility in several different ways, and have implemented the first version of our Environmental Policy to this end.
In our policy we commit to reducing our ecological footprint as much as possible through reducing, reusing, and recycling the resources we utilize.
This includes our data center, servers and other equipment we acquire, where we source our hardware, how we use and power our office spaces, and the communication and transportation involved in our operations.
For the greenhouse gas emissions that do result from our operations and activities we shall compensate doubly.
We will accomplish this by funding the planting of trees through OneTreePlanted sufficient to absorbing twice the amount of greenhouse gas emissions we are responsible for.
Planting trees is the best existing method of capturing carbon from the atmosphere, and has several other beneficial side-effects as well. So we will support rewilding the forests in order to restore and protect ecosystems, our natural environment, and a habitable climate.

We will also encourage partners, stakeholders, and associates to become more environmentally friendly. Furthermore, we will push for the development and implementation of green and renewable technologies and help encourage governments to become more environmentally responsible.
We are extending our commitment to provide free email services to non-profit organizations with an environmentally oriented profile.
We hope to inspire other companies to adopt similar policies and contribute to a positive impact on the only planet we can call home.