As each day goes by there seem to be new revelations about which countries are spying on each other, or have secret agreements to monitor traffic by putting “taps” on strategically important cables entering or leaving countries. It is hard to keep track of all this information, and even harder to verify what is fact and what is speculation.
Questions, questions!
If you care about your data or email and whether it is private or not, then all of this should bother you; in fact it should bother you quite a lot. But how do you make sense of it all, and what action can you take, assuming you can take action that is? Which countries will look after your data best? And who can actually read your email as it is delivered to and from your email provider?
At Runbox we get asked a lot of questions like the ones above, and we have come to the conclusion that often we are worrying about the wrong things.
Who are the players in this real-life James Bond story?
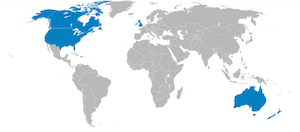 The United States National Security Agency (NSA) and the British Government Communications Headquarters (GCHQ) have featured heavily in the media, and along with three other countries (Canada, Australia and New Zealand) they make up the so called “Five Eyes” countries that are known to be monitoring communications.
The United States National Security Agency (NSA) and the British Government Communications Headquarters (GCHQ) have featured heavily in the media, and along with three other countries (Canada, Australia and New Zealand) they make up the so called “Five Eyes” countries that are known to be monitoring communications.
These countries have an agreement to share data that they collect through their extensive networks. This is not speculation, this is hard fact in the public domain, and together they form the single biggest data sharing network ever conceived. The allegations that they spy on each others citizens and then share data with each other to get around domestic regulations relating to spying on your own citizens is one of the most controversial claims that have been made in the last few years.
There are other revelations that suggest many countries also have agreements with the NSA and GCHQ in return for various kind of technological assistance that might benefit the collaborating nation.
More recently, and closer to home for Runbox, we have seen allegations that Denmark is monitoring data entering and leaving Norway, and that Sweden is pretty much in league with the NSA about as much as the other “five eyes” countries. At a glance this can seem worrying given that Runbox is based in Norway.
But does it really matter?
Data everywhere, and no place to hide
 On a political front it probably does matter, but on a practical level if you email someone who is outside of Norway the chances are the data passes through a number of countries and worrying about the ones geographically adjacent to Norway seems a little pointless. For example, if you email anyone on Gmail, Yahoo, Outlook, iCloud or any of the other major providers, the chance is your data is going to end up in the one country that is at the centre of the recent revelations – the USA.
On a political front it probably does matter, but on a practical level if you email someone who is outside of Norway the chances are the data passes through a number of countries and worrying about the ones geographically adjacent to Norway seems a little pointless. For example, if you email anyone on Gmail, Yahoo, Outlook, iCloud or any of the other major providers, the chance is your data is going to end up in the one country that is at the centre of the recent revelations – the USA.
The reason we get asked questions about security is because people want to take positive action to protect their data, so what can you actually do?
Stored email and data
The question about which email provider will protect your data best when it is on their servers is a separate issue to the one surrounding your data when it is being transferred from one place to another. In respect of your email provider, you are better to keep your email data in a country that has strong privacy laws, and with a provider that tries to encrypt the transfer of that data to and from your account. Runbox is based in a country that does have strong privacy laws, and we always try to encrypt your data when transferring it to and from your account.
So choosing an email provider isn’t too difficult once you know what to look for.
So what about data transfer?
Given that we know agencies are monitoring Internet communications (it doesn’t matter how much or little of this is going on) it is best to assume that anything that you do on the Internet, or anything you email can be monitored by someone. You can think of this as being like sending a private message on a postcard through the usual mail where everyone including the post office and your family can read the postcard.
Fundamentally the data that makes up your email can be read by any server it passes through on its way to its destination. Mail servers also write information to their hard drives and then use that data when sending your email on to the next destination. This means that temporary copies of your email are also made!
There is very little you can do about this, it’s how email works.
 An obvious solution to prevent prying eyes from reading your email is to use some sort of code that only the sender and recipient can decode, and that is exactly what encryption is. If you encrypt a message with a strong enough key then it is currently not possible for anyone to read it without having the private key and passphrase. For now we will ignore allegations that encryption has been subverted by governments as it is clear that strong encryption does still work adequately.
An obvious solution to prevent prying eyes from reading your email is to use some sort of code that only the sender and recipient can decode, and that is exactly what encryption is. If you encrypt a message with a strong enough key then it is currently not possible for anyone to read it without having the private key and passphrase. For now we will ignore allegations that encryption has been subverted by governments as it is clear that strong encryption does still work adequately.
Regardless of whether you encrypt messages yourself, Runbox attempts to encrypt your email when it sends to and receives email from other providers on your behalf. This is an important security feature, but it isn’t universally used and even some major email providers do not offer this kind of encryption. Where it is not offered your email is delivered unencrypted and it is just as vulnerable to interception then as a postcard is.
End-to-end encryption
Email is about 40 years old, and it hasn’t changed much in all that time. For decades computer security experts have been aware of the insecure nature of email, which is why email encryption has been around for about half the time email has existed. Encrypting your  email is not a new idea at all, but as a proportion of email sent very little is encrypted by the sender.
email is not a new idea at all, but as a proportion of email sent very little is encrypted by the sender.
The best overall solution is to encrypt the message before it leaves your computer and not rely on anyone else to protect the data for you. The data can then only be decrypted at the recipients end if the correct key is available and the passphrase for that key is known. This is called end-to-end encryption.
There are various ways in which you can encrypt your email, some involve email client (app/program) like Thunderbird, Outlook or Apple Mail and others are integrated in to the webmail service of email providers.
You don’t need to be an expert to encrypt your email
Encrypting your email is not as difficult as you might think, but you might need to make some changes to how you use email.
We are used to having a very wide variety of email providers at our fingertips, and encryption isn’t necessarily going to be compatible with all of those various interfaces. Elsewhere on this blog and on the Runbox help website we explain some of the easier ways to implement strong email encryption that can be used with most email providers.
Yes, you are going to have to give your friends, family and colleagues keys so they can decrypt email and also send encrypted email to you, but is that really much more difficult than having to give them a key to get in to your home (assuming you want them in your home that is)?
If you encrypt your email it won’t matter what revelations are in the news next week, only you and your recipients will be able to read your email. Unless of course the revelations are about encryption having been compromised…
For more information
Continue Reading →


 On a political front it probably does matter, but on a practical level if you email someone who is outside of Norway the chances are the data passes through a number of countries and worrying about the ones geographically adjacent to Norway seems a little pointless. For example, if you email anyone on Gmail, Yahoo, Outlook, iCloud or any of the other major providers, the chance is your data is going to end up in the one country that is at the centre of the recent revelations – the USA.
On a political front it probably does matter, but on a practical level if you email someone who is outside of Norway the chances are the data passes through a number of countries and worrying about the ones geographically adjacent to Norway seems a little pointless. For example, if you email anyone on Gmail, Yahoo, Outlook, iCloud or any of the other major providers, the chance is your data is going to end up in the one country that is at the centre of the recent revelations – the USA. An obvious solution to prevent prying eyes from reading your email is to use some sort of code that only the sender and recipient can decode, and that is exactly what encryption is. If you encrypt a message with a strong enough key then it is currently not possible for anyone to read it without having the private key and passphrase. For now we will ignore allegations that encryption has been subverted by governments as it is clear that strong encryption does still work adequately.
An obvious solution to prevent prying eyes from reading your email is to use some sort of code that only the sender and recipient can decode, and that is exactly what encryption is. If you encrypt a message with a strong enough key then it is currently not possible for anyone to read it without having the private key and passphrase. For now we will ignore allegations that encryption has been subverted by governments as it is clear that strong encryption does still work adequately. email is not a new idea at all, but as a proportion of email sent very little is encrypted by the sender.
email is not a new idea at all, but as a proportion of email sent very little is encrypted by the sender.